Blockchain sleuth ZachXBT unveils North Korea’s secret crypto empire

- ZachXBT uncovered a North Korean crypto network with $300K-$500K monthly earnings.
- Investigation revealed complex laundering schemes and connections to OFAC-sanctioned individuals.
In a recent investigation, blockchain analyst ZachXBT uncovered a well-coordinated network of North Korean developers.
These developers, involved in crypto, are suspected to earn $300,000-$500,000 monthly.
North Korea crypto scam uncovered
According to his findings shared on the 15th of August, a single entity in Asia, potentially North Korea, likely runs this network.
The group consists of 21 developers working on over 25 crypto projects, revealing significant hidden influence in the global crypto industry.
Providing further insights on the matter, ZachXBT added,
“Unbeknownst to the team they had hired multiple DPRK IT workers as devs who were using fake identities. I then uncovered 25+ crypto projects with related devs that have been active since June 2024.”
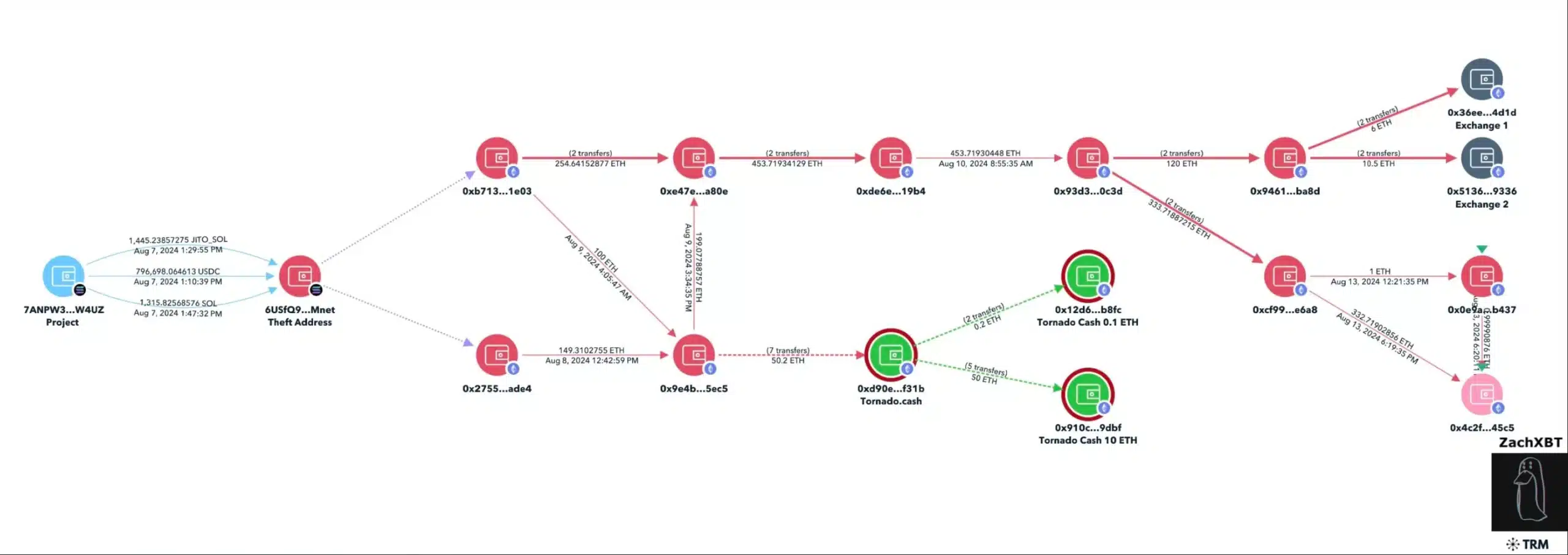
The process involved in the fraud
ZachXBT confirmed that the laundering scheme transfers $1.3M to a theft address bridges it from Solana [SOL] to Ethereum [ETH], deposits 50.2 ETH into Tornado Cash, and then moves 16.5 ETH to two exchanges.
By tracking various payment addresses used by the 21 developers, ZachXBT identified a cluster of recent transactions totaling approximately $375,000 over the past month, revealing a sophisticated network of financial maneuvers.
Who was involved?
For those unaware, before these recent transactions, someone deposited $5.5 million into an exchange address. This address received payments for DPRK IT workers from July 2023 to 2024.
The investigation revealed connections to Sim Hyon Sop, an individual currently sanctioned by the Office of Foreign Assets Control (OFAC).
Additionally, several payment addresses linked to these developers were also associated with Sang Man Kim, a U.S.-sanctioned figure involved in DPRK-related cyber activities.
Kim is suspected of managing DPRK cyber funds and facilitating IT sales to DPRK teams in China and Russia.
In addition, the placement agencies recruited some identified developers, who sometimes referred each other for positions.
“A number of experienced teams have hired these devs so it’s not fair to them single as the ones to blame.”
There’s more to it…
Things took a strange turn when Naoki Murano, a DPRK IT worker identified in ZachXBT’s investigation, abruptly left the chat and deleted his GitHub account in response to the exposure.
Murano’s swift reaction suggests he feared being linked to the network and aimed to minimize his digital footprint.