How Inverse Finance’s $1.2 million exploit played out behind the scenes

The string of DeFi hacks continued to ensue in the crypto market, with the latest victim being Inverse Finance. It suffered a fresh exploit on 16 June worth $1.2 million. It is the latest attack on the protocol after April’s $15.6 million exploits. The PeckShield team released the post-mortem soon after the incident but investors remain on alert.
Another day…another hack
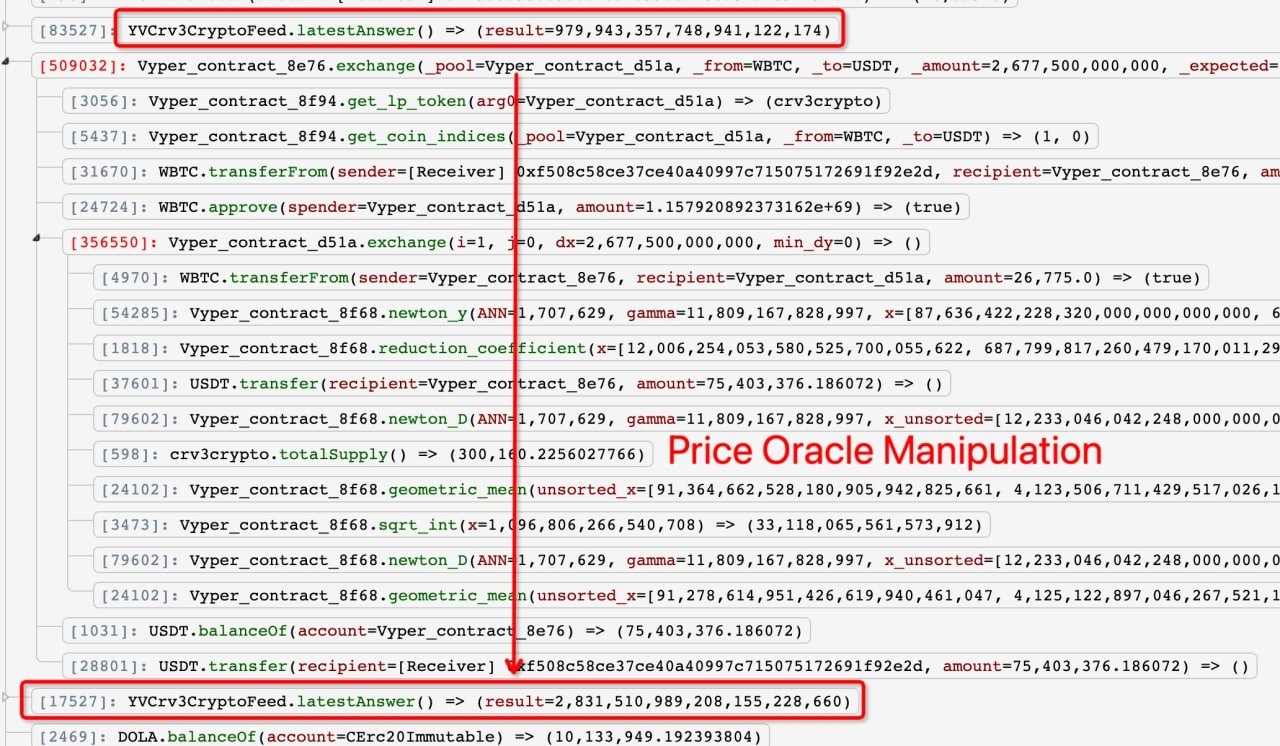
An attacker was able to get away with $1.2 million by exploiting a flash loan on Inverse Finance. The attack was made possible by the price oracle manipulation. As per the Inverse summary, the price of the LP token was manipulated much higher to execute the attack.
Per PeckShield, the attack was started with an initial fund of 1 ETH which is withdrawn from Tornado Cash. Currently, 68 ETHs in illicit gains are resting in the hacker’s account. Another 1000 ETHs were deposited to Tornado Cash afterward.
As per Inverse, this is how the attack came about,
The affected market—yvcrv3crypto—utilized Chainlink price data instead of the internal exchange rate of the Curve protocol, which allowed the attacker to flash-borrow 27,000 in wBTC and trade it into the tri-crypto pool, which caused the price of the yvcrv3crypto LP token to jump in value, in the eyes of the oracle and created an opportunity to borrow DOLA against that collateral in Frontier.”
What now?
The Inverse team released information that DOLA remained resilient against the attack. Moreover, the amount of DOLA liquidity deployed across DOLA Fed contracts also functioned effectively.
Inverse has temporarily paused borrows following an incident this morning where DOLA was removed from our money market, Frontier. We are investigating the incident however no user funds were taken or were at risk. We are investigating and will provide more details soon.
— Inverse+ (@InverseFinance) June 16, 2022
Later, Inverse released news that borrowing has been temporarily paused with DOLA out of their money market. Inverse Finance has also announced measures to get the funds back after the incident. To that end, they announced a ‘generous bounty’ for the attacker(s) if the money was returned. The bounty would also be rewarded for recovering the stolen funds. They have also hired Risk DAO to add additional security operations.
It is now yet to be seen how this incident plays out