Latest in Harmony’s Horizon bridge hack and its technical post-mortem

Harmony, an open and fast layer-1 blockchain offering a two-way Ethereum bridge, suffered an unfortunate hack on 24 June. Horizon, its cross-chain bridge to Ethereum, recorded this exploit worth nearly $100 million in ETH. Although the platform had halted the affected bridge, some questions remain unanswered.
To get a better grip on the situation, here’s a deep dive into what caused this hack.
Exposing the owner, is it?
Security experts of the CertiK team, in a blog posted on 25 June, shared a deep analysis highlighting key events that led to the heist. Wu Blockchain, a famed news agency, later re-shared this development on his Twitter feed.
Certik: The attacker accomplished this by somehow controlling the owner of the MultiSigWallet to call the confirmTransaction() directly to transfer large amounts of tokens from the bridge on Harmony. https://t.co/M1VNahGKcQ
— Wu Blockchain (@WuBlockchain) June 24, 2022
Preliminary analysis showcased that the alleged address made 11 transactions from the bridge for various tokens. Furthermore, the individual sent tokens to a different wallet to swap for ETH on the Uniswap decentralized exchange (DEX), then sent ETH back to the original wallet.
After some further investigation, the expert analysis identified 12 attack transactions and three attack addresses. Across these transactions, the attacker netted various tokens on the bridge including ETH, USDC, WBTC, USDT, DAI, BUSD, AAG, FXS, SUSHI, AAVE, WETH, and FRAX.
“The attacker accomplished this by somehow controlling the owner of the MultiSigWallet to call the confirmTransaction() directly to transfer large amounts of tokens from the bridge on Harmony. This led to a total loss around $97M worth of asset on the Harmony chain which the attacker has consolidated into one main address.”
This event occurred in a sequence as showcased below.
The chain of events
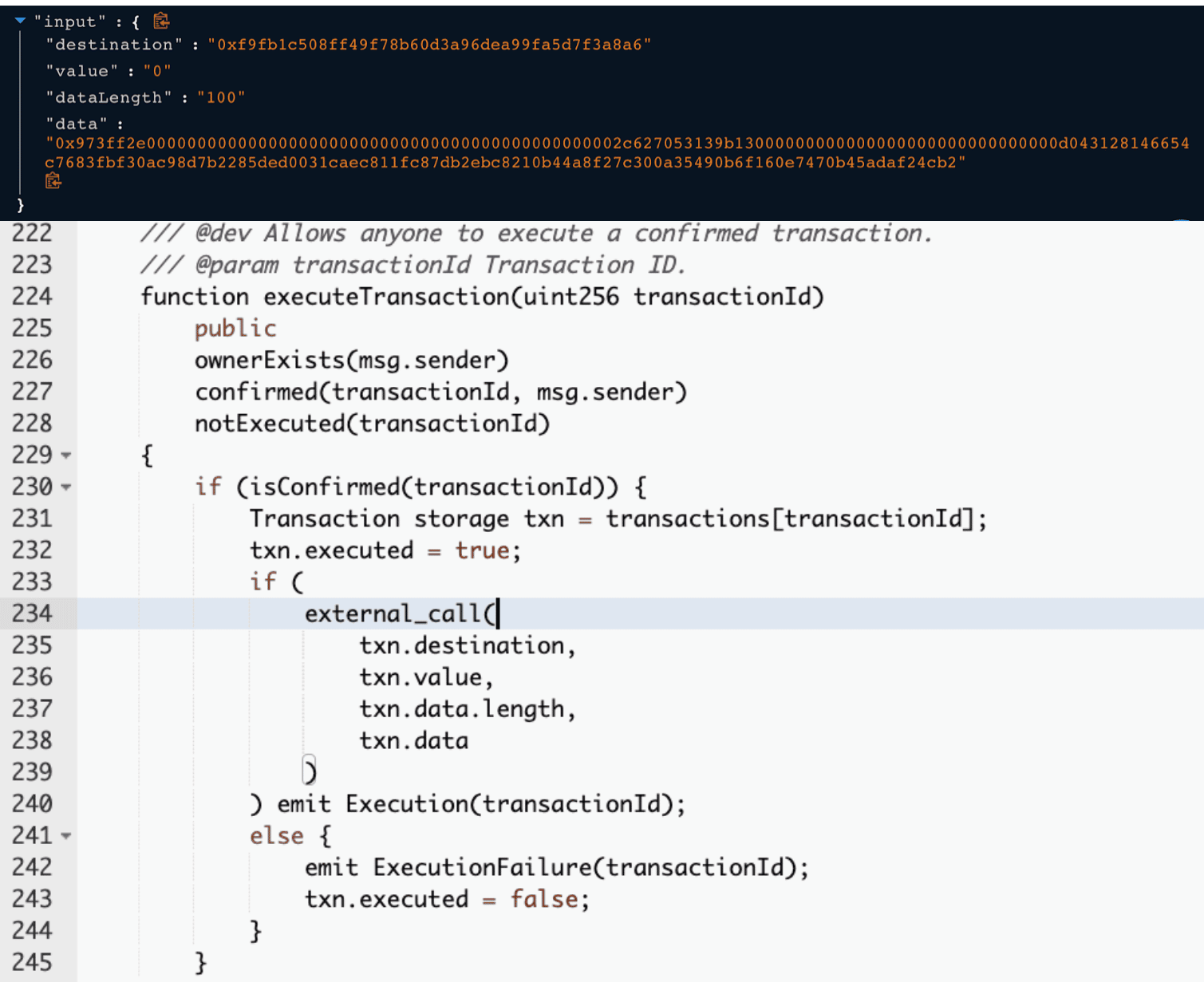
The owner of the MultiSigWallet contract (0xf845a7ee8477ad1fb446651e548901a2635a915) called the submitTransaction() function to submit a transaction. It incorporated the following payload to generate the transaction ID 21106 in the transaction.
Next, in the exploit transaction, the owner called function confirmTransaction() from the MultiSigWallet with the input transaction Id 21106. The executeTransaction() function invoked an external call with input data. This step triggered the unlockEth() function on the Ethmanager contract.
Given the fact that the attacker controlled the owner’s authority, the unlock led the path to the said cross-bridge exploit. The blog also added,
“the attacker executed the transaction with id 21106, which transferred 13,100 ETH to the attacker’s address.”
But that’s not it. The alleged hacker continued the previous process using different transaction IDs on other ERC20Manager contracts to transfer a huge amount of ERC20 tokens and stablecoins.
Overall, such incidents have aggravated the whole skeptical scenario around using cross-chain bridges. Earlier this year we witnessed both the Ronin Bridge exploit and Wormhole exploit.