Transparency or security: Report analyses reasons behind DeFi hacks

After a huge year in 2021, hackers are continuing to target Defi platforms in Q1 2022. Chainalysis reported in a recent study about the increasing trend of malicious activities in the current year.
The bounty was indeed not enough in 2021 when hackers managed to steal $3.2 billion in crypto. They have already managed to scam $1.3 billion in Q1 of 2022. While the money was stolen from exchanges, platforms, and private entities, “the victims are disproportionately in DeFi.”
Let’s talk numbers
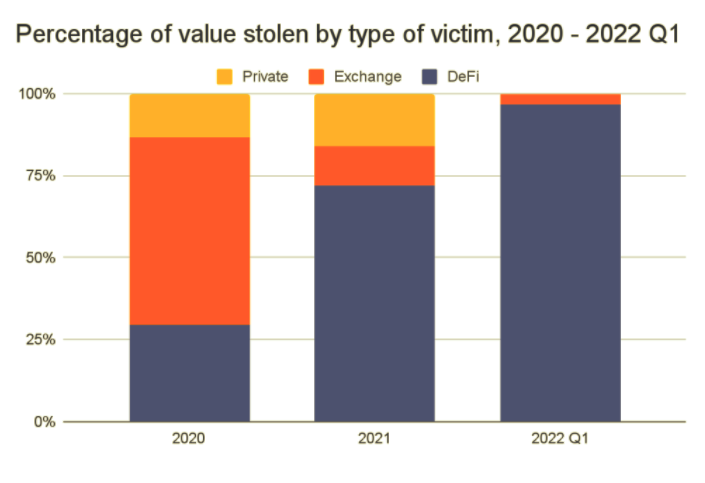
Observing the data below, the developing trend is a worrying one for DeFi communities. The report states,
“Almost 97% of all cryptocurrency stolen in the first three months of 2022 has been taken from DeFi protocols, up from 72% in 2021 and just 30% in 2020.”
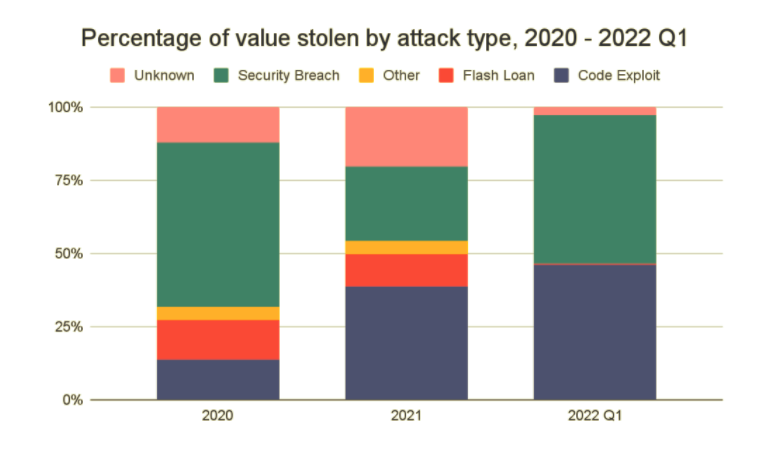
The study also reflects on security breaches that allowed hackers to access victims’ private keys. The $615 million scam on the Ronin Network is one such example. The report confirms this pattern between 2020 and Q1 2022. During this period, 35% of all stolen crypto value is reported due to a security breach.
However, in DeFi protocols, most scams occur due to faulty coding. “Code exploits and flash loan attacks” account for most of the stolen money from such protocols.
As per the report,
“Code exploits occur for a number of reasons. For one, in keeping with DeFi’s faith in decentralization and transparency, open-source development is a staple of DeFi applications.”
The “transparency” factor helps the hackers to plan exploits by scripting vulnerabilities from the code.
Flash loan attacks are caused because of DeFi reliance on price oracles. “Secure but slow oracles are vulnerable to arbitrage; fast but insecure oracles are vulnerable to price manipulation.” While there are solutions for such increasing attacks, it will take time to implement them and ensure safety.
US ties Ronin hack to North Korea group
The U.S has blamed the $615million hack on the Ronin Network on a North Korean hacker group.
“The United States is aware that the DPRK has increasingly relied on illicit activities — including cybercrime — to generate revenue for its weapons of mass destruction and ballistic missile programs as it tries to evade robust U.S. and U.N sanctions,” a Treasury Department spokesperson said.
The group, dubbed as Lazarus, was called out by the spokesperson on a post on the official Ronin blog. It also said that the U.S Treasury Department has sanctioned the address that received the stolen funds.





![Bitcoin [BTC]](https://ambcrypto.com/wp-content/uploads/2025/06/Gladys-5-1-400x240.webp)
