In today’s world, data ownership concerns become more and more relevant. The call for data security grows louder, as centralized data silos fall prey to hackers. Many quote decentralization as the solution to data security concerns, as technologies such as distributed data nodes allow for maximized security. They also provide opportunities for threat isolation and may allow the market to save the $107 billion lost due to identity thefts.
While we look for solutions to protect Public Identifiable Information [PII], companies providing automated KYC solutions have seen a sharp uptick in identity checks for clients in cryptocurrency. This is representative of a market for trusted and automated identity checks. This is the market that the visionaries at Xenchain aim to target.
Xenchain has an existing presence in the market with numerous industry partners onboard. They offer a finished product that is ready for companies to use.
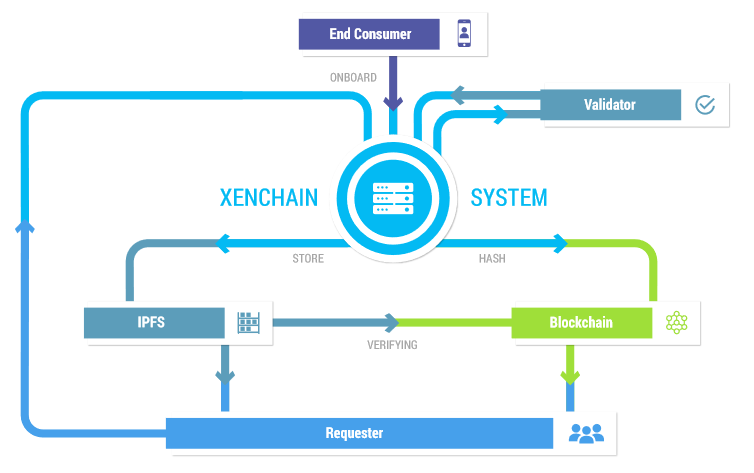
A Xenchain user’s KYC data is encrypted in the IPFS format, and users have full control over their own identity. The blockchain is not storing the plain identity value. Only the hash of the IV parameter from IPFS is stored on the blockchain.
Xenchain: What is it?
Xenchain is a digital identity platform that specializes in gathering and securely storing Public Identifiable Information. It aims to bring data ownership back to the people, with the users having complete control over their data.
Xenchain is a global platform powered by the blockchain for efficiency and for secure, immutable and irrefutable storage of personal information. It brings transparent transaction data to the table using smart contracts on the Ethereum blockchain.
Xenchain also has the ability to provide on-demand, with permission from the user, access to personal data to platforms that support Xenchain through a personal hash. It creates a digital identity on the blockchain for users.
What problems does Xenchain solve?
Even as expenditure towards KYC compliance and accompanying onboarding rose by $150 million, the onboarding time rose from 24 to 32 days. Almost 40% of the world’s population is unbanked and underbanked, putting great pressure on the financial institution to ensure KYC.
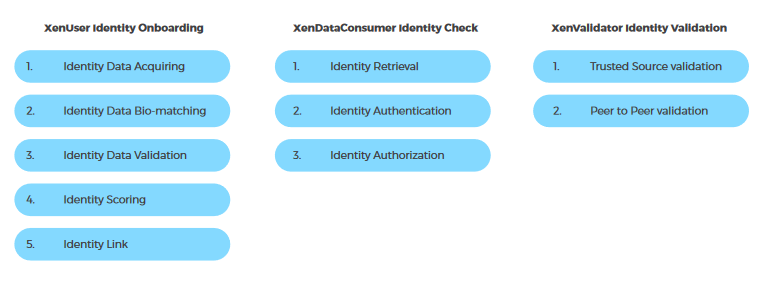
Xenchain’s solution is to introduce a web and mobile app-based platform where individuals can complete the required processes for KYC. It features a 3-part process for the user to create their digital identity on the blockchain.
KYC as a blockchain service will lead to the creation of an immutable, secure and transparent store of PII. The compliance and onboarding charges can be shared by all the parties involved, reducing the overall cost and speed of the process.
Components of Xenchain:
The Xenchain platform is built of 4 components, namely:
- Data Acquisition Module:
The data acquisition module of the Xenchain platform features Optical Character Recognition and AI in the form of Computer Vision. It also features machine learning to determine the validity of the submitted documents. It also features text identifiers, facial recognition and digital ID scanners.
- Data Validation Module:
The data validation module features companies as trusted sources of data. These companies act as referrers to validate data submitted by the user.
- Data Blockchain Module:
The Xenchain platform stores onboarded and verified data on the blockchain and off-chain on distributed storage. The distributed storage facilities feature an InterPlanetary File System for maximum security.
- Data Rating Module:
The platform also features rating for identity data called Xenscore and it also features a social network where users on the platform can interact with each other.
Roles on the Xenchain blockchain:
The Xenchain network features three roles for peers on the blockchain. These roles can be interchanged as per the features and circumstances. They are:
- XenData Consumers:
XenData consumers are corporate entities. Their role is to retrieve and verify an identity from the Xenchain network. The data can be accessed through an enterprise app or an Application Program Interface released by Xenchain.
- XenUser / XenAsset:
XenUsers are natural users whose identities are stored on the blockchain. Their identities include various information fields and unique permissions. XenUsers are connected through a social network on the Xenchain platform.
- XenValidator:
XenValidators are the peers on the blockchain who validate the data collected from XenUsers. They also provide questions for the ID validation.
The verified data is then generated with a unique identifier and a hash public key on the Ethereum blockchain.
The technology behind Xenchain is an intermingling of the best in blockchain, big data, and Artificial Intelligence. The software development kit for the services will be released to Android and iOS programmers by Xenchain, with a gradual transition to open source under the GNU LGPL license.
Onboarding Process:
The onboarding process for XenUsers is comprised of 4 steps.
- Data Acquiring:
The data is acquired through onboarding systems that utilize Optical Character Recognition with computer vision. It also features image recognition, correction and logic processing for checking the validity of ID. ICAO compliant passports, such as Malaysian, Indonesian, Singaporean and Philippines’ passports. The OCR software can process Unicode UTF-16 standard fonts such as Chinese and Thai.
- Bio-matching:
The bio-matching part of the process is to ensure the users’ identity. Through live video recording, the Xenchain software recognizes facial landmarks, eye landmarks and other facial features to match photo ID. The user is prompted to engage in 2 randomly generated movements that ensure that the user is a human being.
- Data validation:
The user is then asked personal questions to determine their validity. These questions come from a credible partner such as credit bureaus, telecom industry and the government’s database. This is then validated in a peer-to-peer fashion, as 3 or more XenUsers with Xenscores of higher than 5 can vet and proof identities. This step also has additional has Anti-Money Laundering checks, along with adverse media and politically exposed person list for screening.
- Data storage:
Due to the highly sensitive nature of the data collected, it will be stored off-chain. The blockchain only contains the hash key and the public key, which will be used to decrypt the off-chain storage. The date will be kept in the IPFS system for distributed storage with SHA256 encryption. The data storage will consist of 2 zones.
Public zone: The ID data in the public zone can be accessed by all.
Private zone: Data is only accessible through permission granted by the XenUser. XenData consumers can access this data with permission. The data stored here will include identity documents and number, addresses and biometric image.
XenScore:
XenScore is used to record the confidence level in data quality. It is on a scale of 1-10 and is used by XenUsers to engage in identity validation.
Xenchain will perform a half-yearly check and validation to the user, challenging them with questions and/or peer-to-peer validation. The verification process is optional, however, and users who decline or unable to verify themselves will have their XenScore will be lowered by 1 point.
Xenchain Utility Token [XEN]:
The XEN token is an ERC20 token used as an incentive instrument to encourage XenValidators to validate identities. The XenUser will also be given XEN when Identity data is shared.
During the ICO the tokens are broken up as follows:
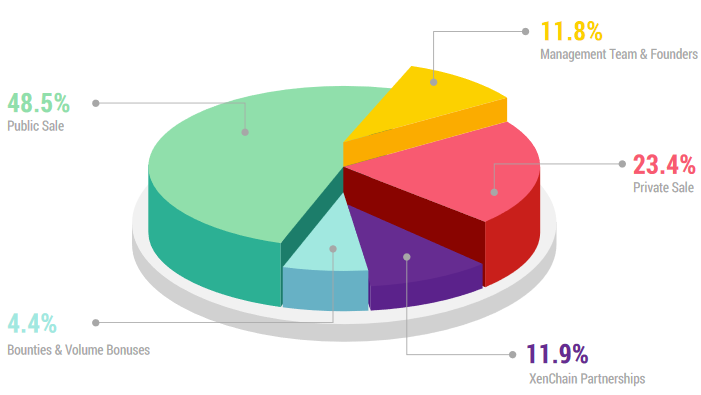
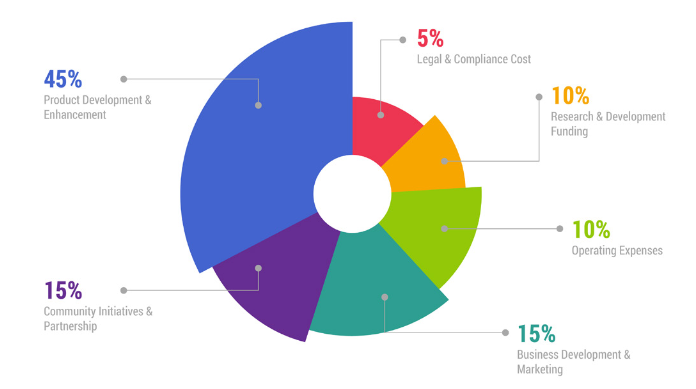
The budget distribution for the Xenchain company is as follows:
The workflow on the Xenchain platform is as follows:
To know more about Xenchain, click here!