Google security report reveals, compromised cloud instances used for crypto mining

Regular mining and mining for cryptocurrencies may not be the same thing, but they do have something in common. Illegal mining of both takes a toll on the environment, the economy, public order and governance. Online attacks have become extremely prominent, and they include cryptocurrency mining abuse, phishing campaigns, ransomware, and so on.
Consider this – a new cyber security report by Google has revealed some alarming statistics. As per this report, the most compromised Google Cloud accounts are used for cryptocurrency mining.
Google’s Cybersecurity Action Team released the first issue of Threat Horizons insights. The report is based on threat intelligence observations from the Threat Analysis Group (TAG), Google Cloud Threat Intelligence for Chronicle, Trust and Safety, and other internal teams.
Source: Google
The report noted:
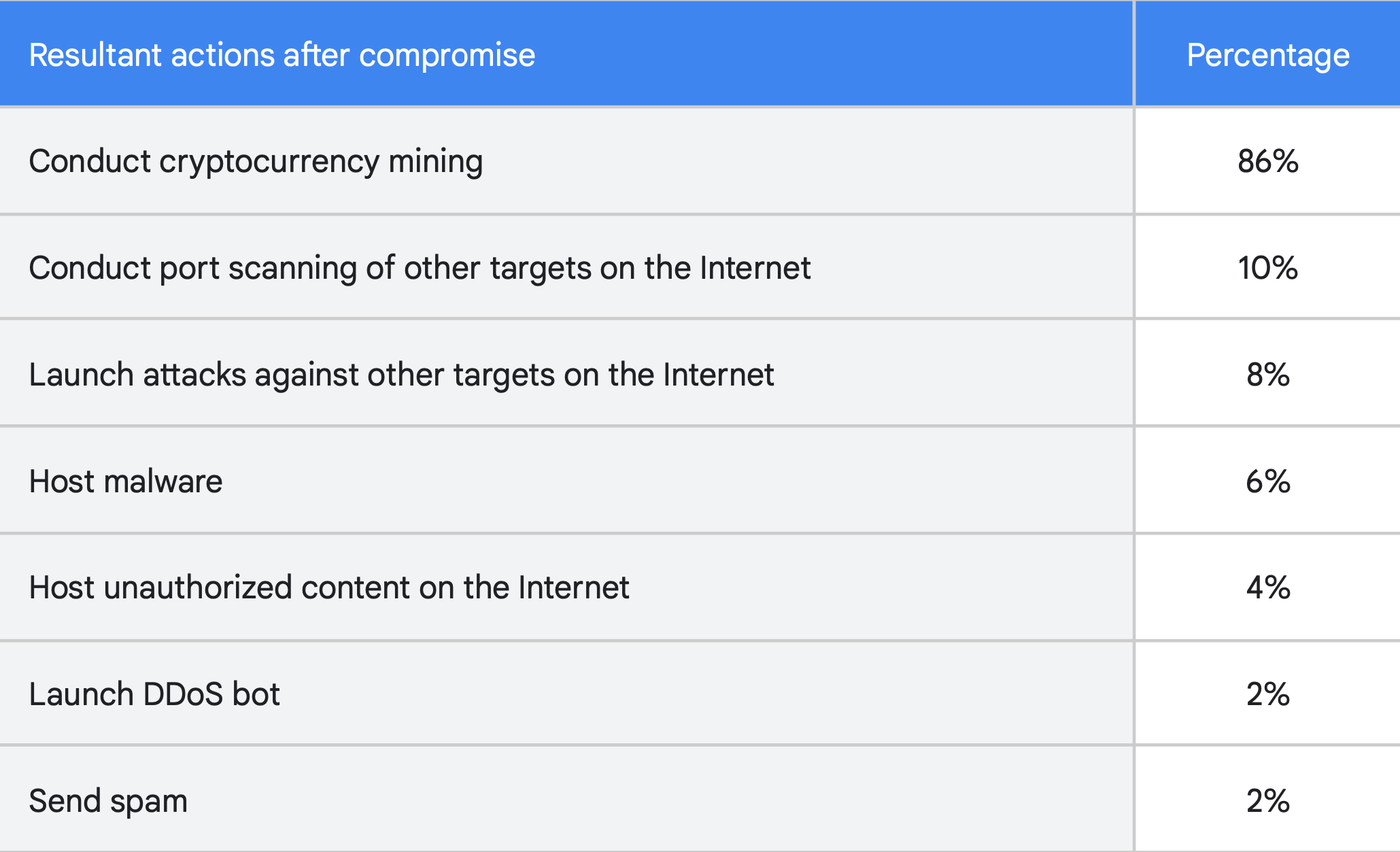
“Of 50 recently compromised GCP instances, 86% of the compromised Google Cloud instances were used to perform cryptocurrency mining, a cloud resource-intensive for-profit activity, which typically consumed CPU/GPU resources, or in cases of Chia mining, storage space.”
Google cloud used for illegal crypto mining
It further added that 10% of the compromised accounts were used to conduct scans of other publicly available internet resources to identify vulnerable systems. Elsewhere, another 8% of the hacked accounts were leveraged to attack other targets.
Well, it also sheds light on possible reasons. For instance, 48% of compromised instances were attributed to actors gaining access to the Internet-facing Cloud instance. These either had no password or a weak password for user accounts or API connections.
The said malicious activities are not new. In fact, the cloud platform is also increasingly witnessing phishing campaigns and ransomware.
“Attackers also continue to exploit poorly configured Cloud instances to obtain profit through cryptocurrency mining and traffic pumping. The universe of ransomware also continues to expand with the discovery of some new ransomware that appears to be offshoots of existing malware with mixed capabilities.”
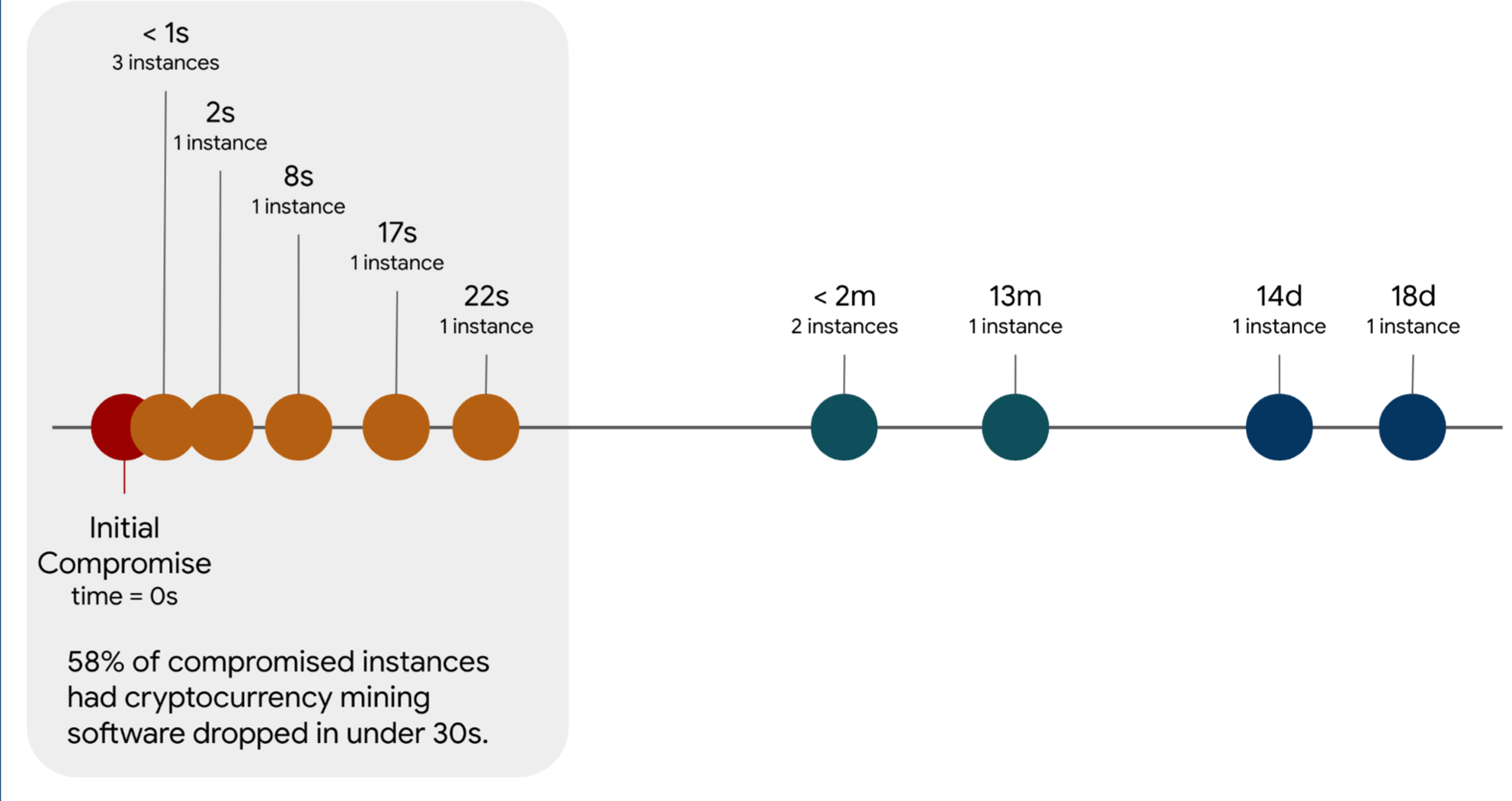
Moving on, time also plays a key role in the compromise of the Google Cloud instances. The shortest amount of time between deploying a vulnerable Cloud instance exposed to the Internet and its compromise was determined to be as little as 30 minutes. Moreover, 58% of cryptocurrency mining software breaches were downloaded within 22 seconds of the account being compromised. The chart below sheds light on this narrative.
Source: Google
What does this signify? Well, looking at the aforementioned timeline, initial attacks and subsequent downloads were scripted events. It didn’t need any human intervention. The report states, “The ability to manually intervene in these situations to prevent exploitation is nearly impossible. The best defense would be to not deploy a vulnerable system or have automated response mechanisms.”
Russian connection
Russian government-backed hacking group APT28, also known as Fancy Bear, attacked about 12,000 Gmail accounts in a mass phishing attempt. Similar to the previously mentioned tasks, these fraudsters would lure to change their credentials on the attacker’s controlled phishing page.
Another hacking involved a North Korea-backed hacker group posing as recruiters at Samsung and sending fake job opportunities to South Korean information security firms’ employees.
In addition to this, another recent report was recently discussed scammers who compromised YouTube videos and cumulatively earned at least $8.9 million in October alone, through fake cryptocurrency giveaways.
Witnessing such a high surge in these malicious activities, improving security by incorporating two-factor authentication (2FA) needs to be a priority.